HACKTHEBOX는 vpn을 통해 메인서버에 접속해 원하는 박스의 문제를 푸는 외국 사이트이다

openvpn에 연결할 vpn을 다운받아서 연결한뒤 문제를 풀것이다
kali리눅스에 openvpn이 기본적으로 설치가 되어있을거다 (아마도?)
안되어있다면 apt-get install을 통해 설치를 하거나 압축파일을 받아 설치하면 된다
openvpn을 설치한뒤 아까 다운받은 vpn파일 위치로 가서
openvpn starting_point_닉네임.ovpn이렇게 명령어를 실행해주면
┌──(root㉿kali)-[/home/kali/Downloads]
└─# openvpn starting_point_tomcat1(2).ovpn
2023-03-06 06:07:01 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless "allow-compression yes" is also set.
2023-03-06 06:07:01 Note: --data-cipher-fallback with cipher 'AES-128-CBC' disables data channel offload.
2023-03-06 06:07:01 OpenVPN 2.6.0 x86_64-pc-linux-gnu [SSL (OpenSSL)] [LZO] [LZ4] [EPOLL] [PKCS11] [MH/PKTINFO] [AEAD] [DCO]
2023-03-06 06:07:01 library versions: OpenSSL 3.0.7 1 Nov 2022, LZO 2.10
2023-03-06 06:07:01 Outgoing Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2023-03-06 06:07:01 Outgoing Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2023-03-06 06:07:01 Incoming Control Channel Encryption: Cipher 'AES-256-CTR' initialized with 256 bit key
2023-03-06 06:07:01 Incoming Control Channel Encryption: Using 256 bit message hash 'SHA256' for HMAC authentication
2023-03-06 06:07:01 TCP/UDP: Preserving recently used remote address: [AF_INET]23.19.225.233:443
2023-03-06 06:07:01 Socket Buffers: R=[131072->131072] S=[16384->16384]
2023-03-06 06:07:01 Attempting to establish TCP connection with [AF_INET]23.19.225.233:443
2023-03-06 06:07:01 TCP connection established with [AF_INET]23.19.225.233:443
2023-03-06 06:07:01 TCPv4_CLIENT link local: (not bound)
2023-03-06 06:07:01 TCPv4_CLIENT link remote: [AF_INET]23.19.225.233:443
2023-03-06 06:07:01 TLS: Initial packet from [AF_INET]23.19.225.233:443, sid=05238ed2 3805b7bd
2023-03-06 06:07:02 VERIFY OK: depth=1, CN=HackTheBox
2023-03-06 06:07:02 VERIFY KU OK
2023-03-06 06:07:02 Validating certificate extended key usage
2023-03-06 06:07:02 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication
2023-03-06 06:07:02 VERIFY EKU OK
2023-03-06 06:07:02 VERIFY OK: depth=0, CN=htb
2023-03-06 06:07:02 Control Channel: TLSv1.3, cipher TLSv1.3 TLS_AES_256_GCM_SHA384, peer certificate: 2048 bit RSA, signature: RSA-SHA256
2023-03-06 06:07:02 [htb] Peer Connection Initiated with [AF_INET]23.19.225.233:443
2023-03-06 06:07:02 TLS: move_session: dest=TM_ACTIVE src=TM_INITIAL reinit_src=1
2023-03-06 06:07:02 TLS: tls_multi_process: initial untrusted session promoted to trusted
2023-03-06 06:07:02 PUSH: Received control message: 'PUSH_REPLY,route 10.10.10.0 255.255.254.0,route 10.129.0.0 255.255.0.0,route-ipv6 dead:beef::/64,tun-ipv6,route-gateway 10.10.16.1,topology subnet,ping 10,ping-restart 120,ifconfig-ipv6 dead:beef:4::100f/64 dead:beef:4::1,ifconfig 10.10.16.17 255.255.254.0,peer-id 0,cipher AES-256-CBC'
2023-03-06 06:07:02 OPTIONS IMPORT: timers and/or timeouts modified
2023-03-06 06:07:02 OPTIONS IMPORT: --ifconfig/up options modified
2023-03-06 06:07:02 OPTIONS IMPORT: route options modified
2023-03-06 06:07:02 OPTIONS IMPORT: route-related options modified
2023-03-06 06:07:02 OPTIONS IMPORT: peer-id set
2023-03-06 06:07:02 OPTIONS IMPORT: data channel crypto options modified
2023-03-06 06:07:02 net_route_v4_best_gw query: dst 0.0.0.0
2023-03-06 06:07:02 net_route_v4_best_gw result: via 192.168.79.2 dev eth0
2023-03-06 06:07:02 ROUTE_GATEWAY 192.168.79.2/255.255.255.0 IFACE=eth0 HWADDR=00:0c:29:00:ae:d5
2023-03-06 06:07:02 GDG6: remote_host_ipv6=n/a
2023-03-06 06:07:02 net_route_v6_best_gw query: dst ::
2023-03-06 06:07:02 sitnl_send: rtnl: generic error (-101): Network is unreachable
2023-03-06 06:07:02 ROUTE6: default_gateway=UNDEF
2023-03-06 06:07:02 TUN/TAP device tun0 opened
2023-03-06 06:07:02 net_iface_mtu_set: mtu 1500 for tun0
2023-03-06 06:07:02 net_iface_up: set tun0 up
2023-03-06 06:07:02 net_addr_v4_add: 10.10.16.17/23 dev tun0
2023-03-06 06:07:02 net_iface_mtu_set: mtu 1500 for tun0
2023-03-06 06:07:02 net_iface_up: set tun0 up
2023-03-06 06:07:02 net_addr_v6_add: dead:beef:4::100f/64 dev tun0
2023-03-06 06:07:02 net_route_v4_add: 10.10.10.0/23 via 10.10.16.1 dev [NULL] table 0 metric -1
2023-03-06 06:07:02 net_route_v4_add: 10.129.0.0/16 via 10.10.16.1 dev [NULL] table 0 metric -1
2023-03-06 06:07:02 add_route_ipv6(dead:beef::/64 -> dead:beef:4::1 metric -1) dev tun0
2023-03-06 06:07:02 net_route_v6_add: dead:beef::/64 via :: dev tun0 table 0 metric -1
2023-03-06 06:07:02 Data Channel: using negotiated cipher 'AES-256-CBC'
2023-03-06 06:07:02 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
2023-03-06 06:07:02 Outgoing Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication
2023-03-06 06:07:02 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key
2023-03-06 06:07:02 Incoming Data Channel: Using 256 bit message hash 'SHA256' for HMAC authentication
2023-03-06 06:07:02 Initialization Sequence Completed마지막줄에 Initialization sequence completed 가 뜨면 잘 실행이 된것이다

나는 HACKTHEBOX가 처음이고 웹해킹 공부도 이제 막 시작한 수준이라 Starting Point 문제부터 천천히 풀어보기로 했다

tag를 통해 어떤 문제인지 대략적으로 알려주고 spawn machine을 통해 머신을 실행시키면 문제를 풀 수 있다

machine을 키면 target ip를 준다 이건 킬때마다 바뀜
이걸 키고 문제를 하나하나 풀어가면 됨
Starting Point라서 그런가 기본적인 문제를 바탕으로 하나하나 알려주며 flag에 도달할 수 있도록 하는거 같다
천천히 풀어보자

1번 문제는 뭐 간단히 약자 문제다 VM이 뭔지 물어보니 답은 virtual machine

2번 문제도 console과 shell로도 불리고 명령어 실행을 해주는 친구니 답은 terminal
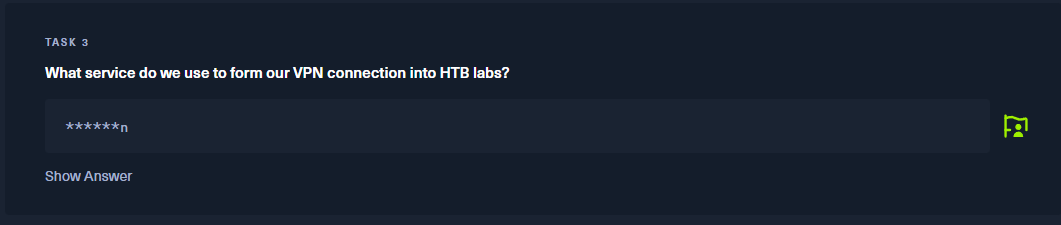
3번 문제는 htb labs를 들어올떄 어떤 vpn을 썻냐고 물어보니 답은 openvpn

4번 문제는 tunnel interface의 약어를 물어본다 답은 tun

5번 문제 ICMP echo request를 사용해 연결 테스트를 하는건 ping이다

6번 문제 열려있는 포트를 찾기위해 가장 일반적으로 사용되는 툴은 Nmap이다
하지만 Nmap을 통해 허가되지 않은 페이지를 포트스캔하는 것은 불법이니 문제를 풀거나 허가된곳만 사용해야한다

7번 문제 이 문제는 23번 포트가 접속가능한지 확인할때 뭘 써야하는지 묻는거 같은데
문제 tag에 나왔듯 telnet을 사용하면 될거같다
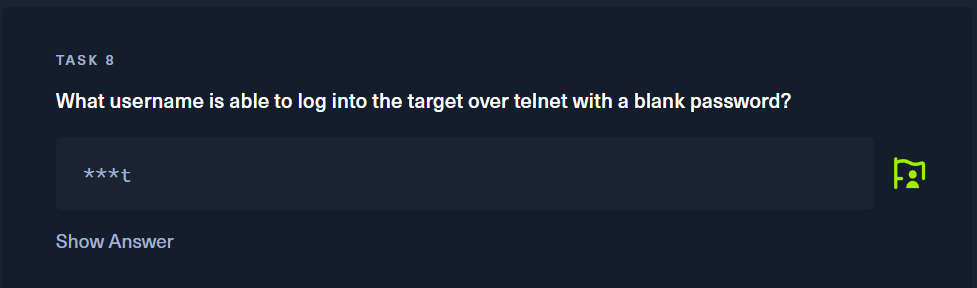
8번 문제 암호없이 텔넷을 통해 접속할 수 있는 계정은 보통 admin 아니면 root계정인데 끝이 t인걸 보니 root 인거같다

이제 플래그를 얻어야 하는데 앞에 알려준 것들을 차근차근 하면 된다
┌──(root㉿kali)-[~]
└─# ping 10.129.76.159
PING 10.129.76.159 (10.129.76.159) 56(84) bytes of data.
64 bytes from 10.129.76.159: icmp_seq=1 ttl=63 time=193 ms
64 bytes from 10.129.76.159: icmp_seq=2 ttl=63 time=193 ms
64 bytes from 10.129.76.159: icmp_seq=3 ttl=63 time=193 ms
64 bytes from 10.129.76.159: icmp_seq=4 ttl=63 time=193 ms
64 bytes from 10.129.76.159: icmp_seq=5 ttl=63 time=225 ms
^C
--- 10.129.76.159 ping statistics ---
6 packets transmitted, 5 received, 16.6667% packet loss, time 5018ms
rtt min/avg/max/mdev = 193.002/199.570/225.321/12.875 ms먼저 핑을 보내서 접속가능한 포트인지 확인하고
┌──(root㉿kali)-[~]
└─# nmap -A 10.129.76.159
Starting Nmap 7.93 ( https://nmap.org ) at 2023-03-06 06:56 EST
Nmap scan report for 10.129.76.159
Host is up (0.38s latency).
Not shown: 999 closed tcp ports (reset)
PORT STATE SERVICE VERSION
23/tcp open telnet Linux telnetd
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.93%E=4%D=3/6%OT=23%CT=1%CU=43776%PV=Y%DS=2%DC=T%G=Y%TM=6405D514
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=FC%GCD=1%ISR=106%TI=Z%CI=Z%II=I%TS=A)OPS(O
OS:1=M53AST11NW7%O2=M53AST11NW7%O3=M53ANNT11NW7%O4=M53AST11NW7%O5=M53AST11N
OS:W7%O6=M53AST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6=FE88)ECN(R
OS:=Y%DF=Y%T=40%W=FAF0%O=M53ANNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%F=AS%
OS:RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T5(R=Y
OS:%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R
OS:%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=
OS:40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40%CD=S
OS:)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 428.61 ms 10.10.16.1
2 192.93 ms 10.129.76.159
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 54.05 secondsnmap을 통해 스캔해보면 23번 포트가 telnet을 통해 open되어 있음을 확인했고
┌──(root㉿kali)-[~]
└─# telnet 10.129.76.159
Trying 10.129.76.159...
Connected to 10.129.76.159.
Escape character is '^]'.
█ █ ▐▌ ▄█▄ █ ▄▄▄▄
█▄▄█ ▀▀█ █▀▀ ▐▌▄▀ █ █▀█ █▀█ █▌▄█ ▄▀▀▄ ▀▄▀
█ █ █▄█ █▄▄ ▐█▀▄ █ █ █ █▄▄ █▌▄█ ▀▄▄▀ █▀█
Meow login:telnet을 통해 접속하면 로그인 하라고 뜨는데 위에서 비밀번호 없이 접속가능한 아이디가 root라고 했으니
Meow login: root
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-77-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Mon 06 Mar 2023 11:51:20 AM UTC
System load: 0.0
Usage of /: 41.7% of 7.75GB
Memory usage: 4%
Swap usage: 0%
Processes: 136
Users logged in: 0
IPv4 address for eth0: 10.129.76.159
IPv6 address for eth0: dead:beef::250:56ff:feb9:afc0
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
75 updates can be applied immediately.
31 of these updates are standard security updates.
To see these additional updates run: apt list --upgradable
The list of available updates is more than a week old.
To check for new updates run: sudo apt update
Last login: Mon Sep 6 15:15:23 UTC 2021 from 10.10.14.18 on pts/0
root@Meow:~# ls
flag.txt snap
root@Meow:~# cat flag.txt루트계정을 통해 접속후 flag를 찾아내면 된다

tag옆에 있는 Walkthrough를 통해 문제를 푸는 과정을 볼 수 있다 이걸로 정답을 확인하는게 더 좋을 수 있다
'WAR GAME' 카테고리의 다른 글
| [Dreamhack] xss-2 (0) | 2023.03.30 |
|---|---|
| [Dreamhack] xss-1 (0) | 2023.03.30 |
| [Dreamhack] cookie (0) | 2023.03.30 |
| [Dreamhack] session-basic (0) | 2023.03.29 |
| H4CKING GAME - Qualification (2) | 2022.08.10 |